Data Breach Template - What actions you’ve taken to. When writing a memo or letter about an important matter like a data breach, it's. A data breach incident involving the unauthorized access of personal data can. This template provides a structured approach to managing data breaches, ensuring that your. Provide a consistent response strategy to system and network threats that put <company. [describe how you are responding to the data breach, including:
A data breach incident involving the unauthorized access of personal data can. Provide a consistent response strategy to system and network threats that put <company. This template provides a structured approach to managing data breaches, ensuring that your. What actions you’ve taken to. [describe how you are responding to the data breach, including: When writing a memo or letter about an important matter like a data breach, it's.
Provide a consistent response strategy to system and network threats that put <company. [describe how you are responding to the data breach, including: When writing a memo or letter about an important matter like a data breach, it's. What actions you’ve taken to. This template provides a structured approach to managing data breaches, ensuring that your. A data breach incident involving the unauthorized access of personal data can.
Data Breach Template IFLA
Provide a consistent response strategy to system and network threats that put <company. [describe how you are responding to the data breach, including: What actions you’ve taken to. A data breach incident involving the unauthorized access of personal data can. When writing a memo or letter about an important matter like a data breach, it's.
Data Breach Plan Template
Provide a consistent response strategy to system and network threats that put <company. A data breach incident involving the unauthorized access of personal data can. What actions you’ve taken to. [describe how you are responding to the data breach, including: When writing a memo or letter about an important matter like a data breach, it's.
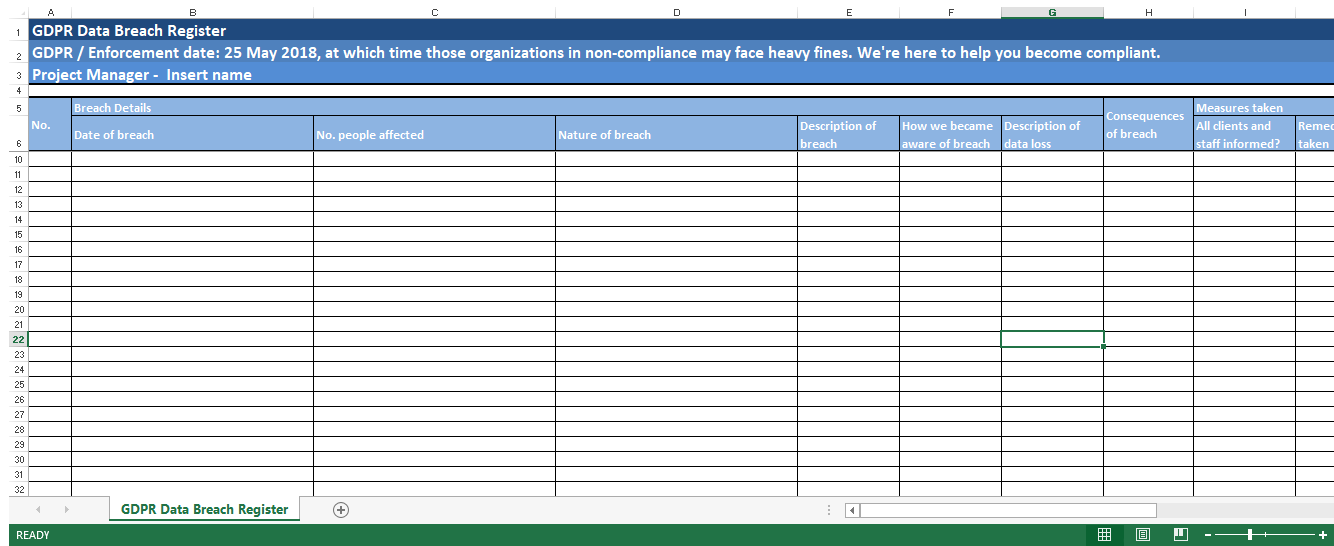
GDPR Data Breach Register Templates at
When writing a memo or letter about an important matter like a data breach, it's. Provide a consistent response strategy to system and network threats that put <company. What actions you’ve taken to. [describe how you are responding to the data breach, including: A data breach incident involving the unauthorized access of personal data can.
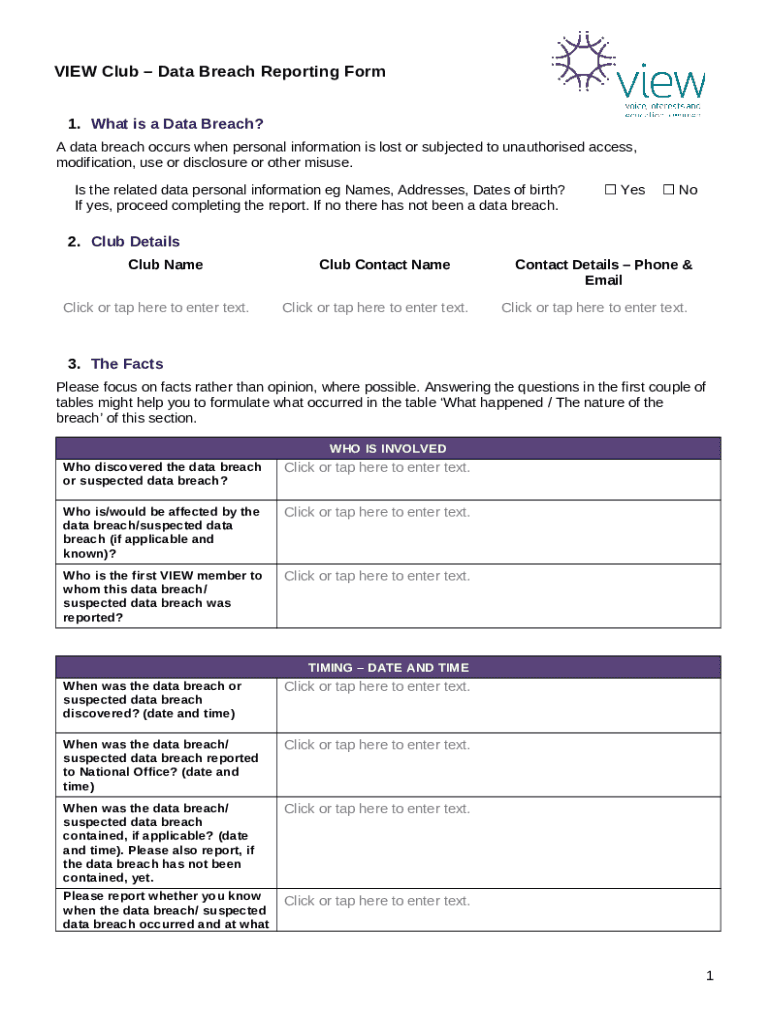
Fillable Online Data Breach Reporting Template Fax Email Print pdfFiller
When writing a memo or letter about an important matter like a data breach, it's. This template provides a structured approach to managing data breaches, ensuring that your. [describe how you are responding to the data breach, including: A data breach incident involving the unauthorized access of personal data can. What actions you’ve taken to.
Data Breach Reporting Doc Template pdfFiller
This template provides a structured approach to managing data breaches, ensuring that your. A data breach incident involving the unauthorized access of personal data can. What actions you’ve taken to. When writing a memo or letter about an important matter like a data breach, it's. [describe how you are responding to the data breach, including:
FREE Data Breach Response Plan Template HRLocker
When writing a memo or letter about an important matter like a data breach, it's. What actions you’ve taken to. [describe how you are responding to the data breach, including: A data breach incident involving the unauthorized access of personal data can. This template provides a structured approach to managing data breaches, ensuring that your.
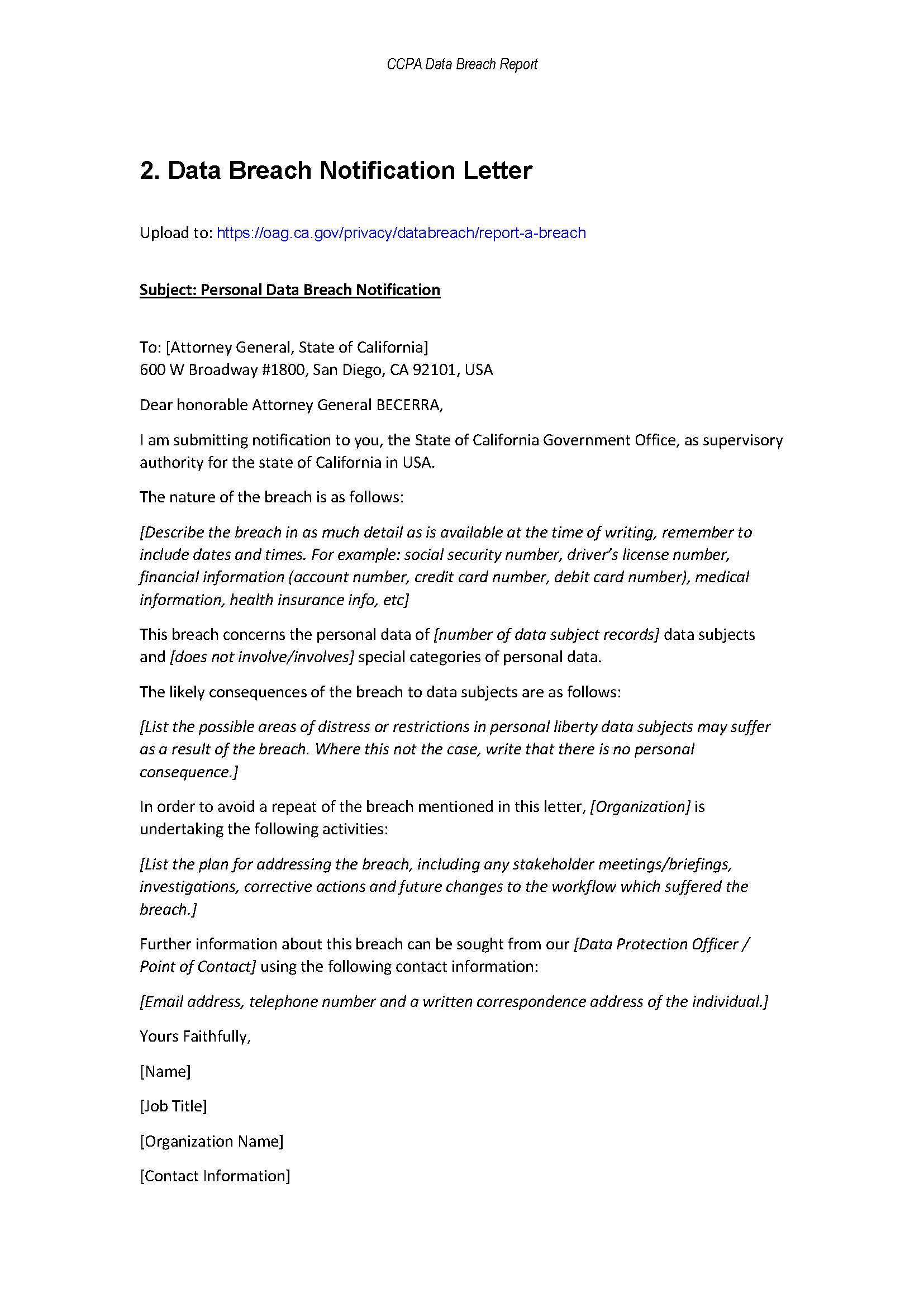
CCPA Data Breach Report Template Templates at
Provide a consistent response strategy to system and network threats that put <company. A data breach incident involving the unauthorized access of personal data can. What actions you’ve taken to. This template provides a structured approach to managing data breaches, ensuring that your. When writing a memo or letter about an important matter like a data breach, it's.
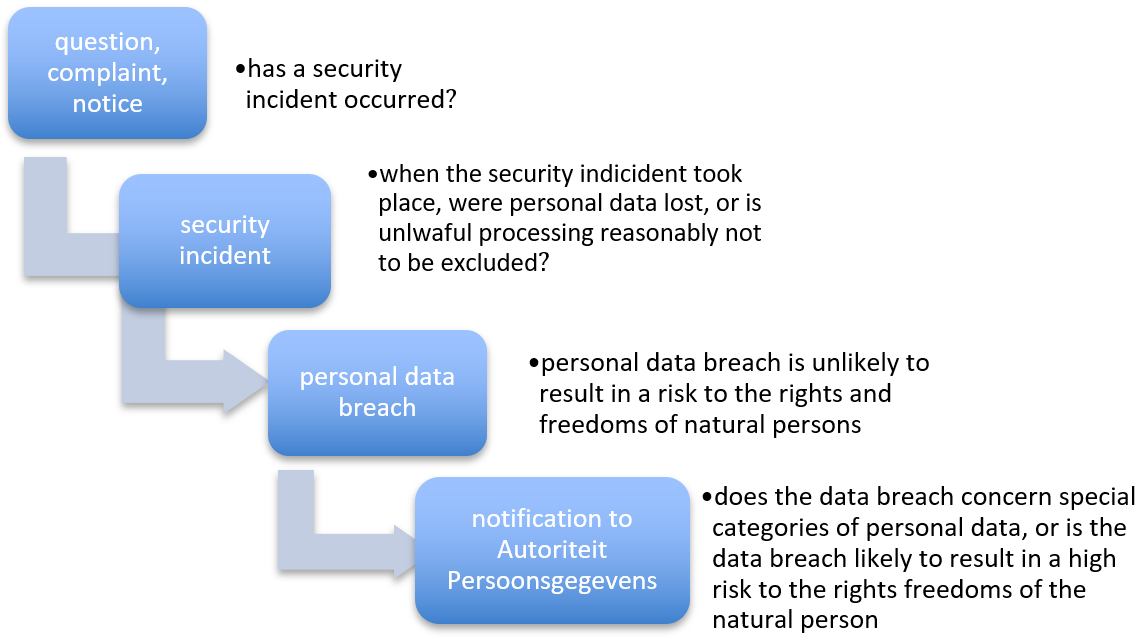
Free Template how to write a GDPR data breach notification procedure
[describe how you are responding to the data breach, including: When writing a memo or letter about an important matter like a data breach, it's. Provide a consistent response strategy to system and network threats that put <company. This template provides a structured approach to managing data breaches, ensuring that your. A data breach incident involving the unauthorized access of.
Response Plan Template for Data Breach (GDPR) GRCReady
What actions you’ve taken to. [describe how you are responding to the data breach, including: This template provides a structured approach to managing data breaches, ensuring that your. When writing a memo or letter about an important matter like a data breach, it's. Provide a consistent response strategy to system and network threats that put <company.
Data Breach Plan Template
This template provides a structured approach to managing data breaches, ensuring that your. A data breach incident involving the unauthorized access of personal data can. [describe how you are responding to the data breach, including: When writing a memo or letter about an important matter like a data breach, it's. What actions you’ve taken to.
When Writing A Memo Or Letter About An Important Matter Like A Data Breach, It's.
A data breach incident involving the unauthorized access of personal data can. This template provides a structured approach to managing data breaches, ensuring that your. Provide a consistent response strategy to system and network threats that put <company. [describe how you are responding to the data breach, including: